You have not yet added any article to your bookmarks!

Join 10k+ people to get notified about new posts, news and tips.
Do not worry we don't spam!
Post by : Anis Farhan
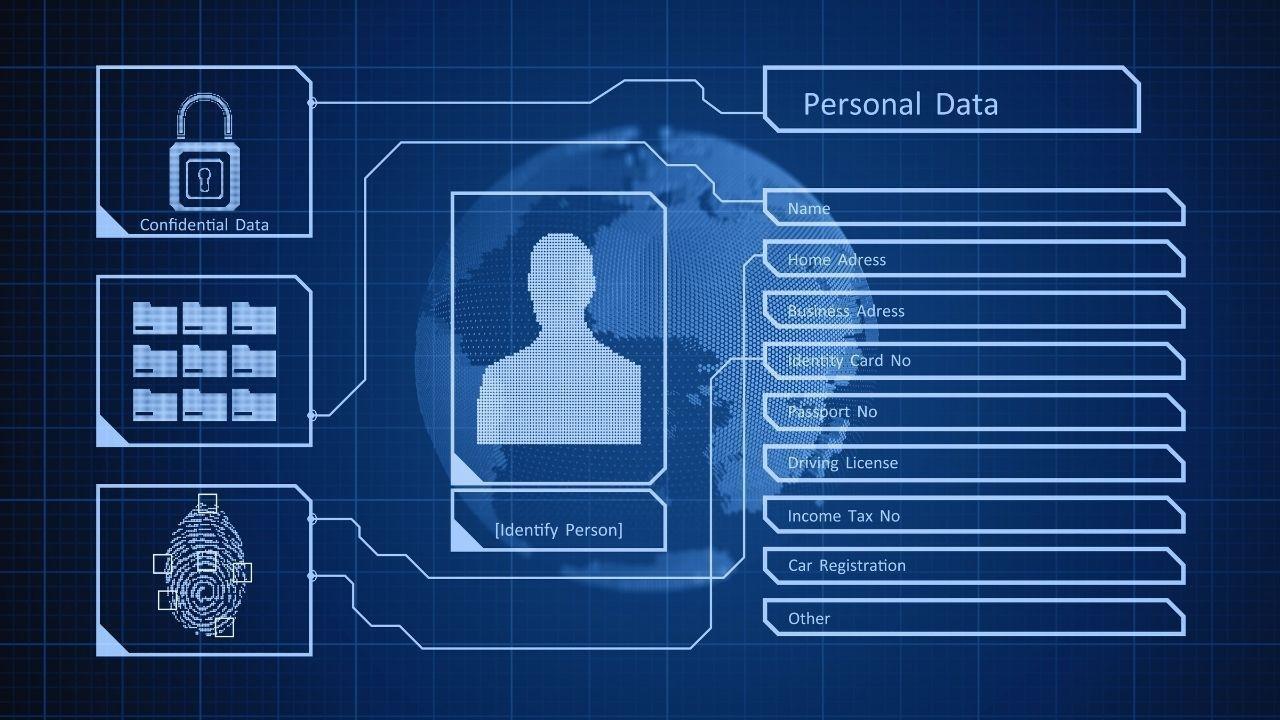
As the need for digital identity solutions escalates, two major forces—scale and risk—are converging. With an increasing number of services, users, and devices, the daily interactions involving identity multiply. Simultaneously, these systems are under constant threats including phishing, credential theft, and sophisticated cyber-attacks, rendering traditional username-password models outdated.
Organizations are now challenged to transition to a paradigm that ensures users can access services in a passwordless manner (eliminating the need for users to remember or manage passwords), maintains privacy (so user identities aren’t unnecessarily exposed), and guarantees security (preventing attacks before they occur rather than simply detecting them). Achieving all three—passwordless, private, and secure—simultaneously is not as straightforward as it appears.
Passwordless authentication eliminates reliance on the traditional "something you know" (password) by substituting it with either "something you have" (devices, tokens) or "something you are" (biometric identifiers), or often a mix of both. This evolution reduces common security vulnerabilities associated with forgotten or stolen secrets.
Privacy in identity verification means not unnecessarily storing or sharing user data and minimizing the transfer of information between parties. It empowers users to control their own identity attributes—allowing them to decide what they share and with whom.
Security entails creating an identity system that can withstand known threats such as credential stuffing, phishing, and supply-chain vulnerabilities. It also signifies having established standards, audit capabilities, encryption protocols, and proven sustainable practices.
Though each of these areas is significant individually, the real difficulty lies in crafting a solution that holistically guarantees all three.
Standards like WebAuthn and FIDO2 signal a shift from passwords towards cryptographic keys linked to devices and unlocked using biometrics or PINs. Due to the absence of stored passwords, susceptibility to phishing attacks declines markedly.
Rather than centralization, which involves service providers managing credentials, the trend towards self-sovereign identity allows users to control their data attributes and share them selectively. Innovations like decentralized biometric authentication are finding their stride in research.
Platforms are increasingly favoring biometric systems that retain data on the user's device, ensuring that biometric information cannot be exploited. This approach allows for seamless authentication while addressing privacy concerns.
Modern identity solutions are embracing passwordless workflows and biometric integrations to streamline the transition from traditional credential systems to more secure digital frameworks.
With heightened scrutiny concerning identity, privacy, and data security, organizations are pressed to pursue secure, privacy-centric identity schemes, driving both innovation and adoption among vendors.
By eliminating passwords, many common attacks become significantly less feasible. Organizations that opt for device-linked credentials experience a marked decline in credential theft incidents.
With the removal of passwords, users enjoy a smoother experience, leading to enhanced engagement and conversion rates as procedures like passkeys result in faster logins.
The costs associated with managing passwords—including help-desk activities for resets—can be dramatically reduced by implementing passwordless solutions.
By migrating identity verification to user-controlled devices, organizations reduce privacy risks, fostering user trust and regulatory compliance.
Businesses employing sophisticated identity solutions will be in a favorable position to meet evolving cyber threats and regulatory demands.
Device-linked authentication carries risks, such as loss of the device or access issues, necessitating robust recovery solutions that do not undermine security.
Many organizations remain reliant on older systems, complicating the shift to a fully passwordless model and necessitating integration with existing frameworks.
Though users desire convenience, they might not grasp the implications of security measures in device-bound biometrics. Audits and transparent practices are vital.
Even without passwords, identity systems face myriad threats necessitating holistic security architectures to combat various vulnerabilities.
While standards like FIDO2 exist, comprehensive support across platforms remains inconsistent, posing potential risks to user experience and security.
Even optimal systems can falter if user enrollment and device configurations are poor. Continued support and education are critical for success.
Determine areas with the highest identity risks, such as remote access and third-party interactions. Understanding failure costs can channel efforts into prioritizing identity solutions.
Evaluate your identity ecosystem, credential methods, and access flows to define a roadmap for integrating passwordless solutions, considering the complexities of legacy systems.
Opt for identity solutions that align with established standards and privacy-driven architecture to ensure effective security and user data management.
Establish reliable fallback systems for scenarios where device loss occurs, ensuring that user accounts can be recovered securely.
Regularly assess metrics to gauge authentication efficiency and user satisfaction trends to justify further implementations and strategic transformations.
Clearly communicate system changes to users to alleviate concerns and foster engagement with new identity protocols. User comfort is paramount.
Include considerations for emerging technologies like quantum-resistant security in your strategy to remain ahead of potential future challenges.
Big service providers are increasingly adopting passkeys as the standard for new accounts, transforming the underlying identity paradigm.
Self-sovereign identity models utilizing blockchain and user-managed credentials are set to gain traction and real-world validation.
Sector-sensitive areas will prioritize systems where biometric data is authenticated on-device, eliminating central storage risks.
Identity solutions being integrated into zero-trust frameworks will enhance security, positioning identity as a core trust mechanism beyond traditional perimeters.
Tighter regulations around identity frameworks will press organizations to adopt robust privacy features and compliance measures.
With advancements in quantum computing, there will be a compelling need for identity systems to adapt quantum-resistant algorithms to protect sensitive credentials.
The progress towards digital identity solutions that are both passwordless and secure is evident, with numerous organizations on this path. However, realizing the ideal balance is not guaranteed. Operational trade-offs remain, and success requires addressing legacy systems, enhancing recovery pathways, and ensuring user adaptation without compromising holistic security. Those who recognize identity as a strategic resource will be prepared for a future where passwords diminish, privacy becomes paramount, and addressing identity threats is significantly more challenging.










Study Warns Using AI for Medical Advice Is ‘Dangerous’ as Users Get Inaccurate Health Guidance
A major new study reveals that artificial intelligence (AI) chatbots and tools may give misleading o

Top Sci-Fi Movies Streaming on Netflix This February: Must-Watch Picks for Genre Fans
A curated news-style guide to the best science fiction films currently available on Netflix in Febru

BCCI Central Contracts Shake-Up: Kohli, Rohit Moved to Grade B as Board Reshapes 2025–26 List
Virat Kohli and Rohit Sharma have been placed in Grade B in the BCCI’s 2025–26 central contract list

Dalal Street Spotlight: Top 10 Stocks Investors Are Watching as Markets Open on a High
Indian stock markets begin the week with strong momentum, and several blue-chip and mid-cap stocks a

Market Movers Today: Key Stocks Set To Watch In Indian Markets
Indian equity markets are poised for active trading as several major companies, including Bharti Air

Milan Welcomes the World: Inside the Grand Opening Ceremony of the 2026 Winter Olympics
The 2026 Winter Olympics opening ceremony in Milan marked a defining moment for global sport, blendi