
Join 10k+ people to get notified about new posts, news and tips.
Do not worry we don't spam!
Post by : Anis Farhan
Quantum cryptography promises to secure information by harnessing the principles of quantum physics rather than relying solely on computational difficulty. With growing investment in quantum computing and networks, industry and policymakers are asking not whether this technology matters but when it will start to reshape digital security.
Encryption is the backbone of modern life — protecting mobile banking, private messaging, medical files and national systems. Much of today’s protection depends on mathematical tasks deemed infeasible for classical machines. Quantum computers threaten to overturn those assumptions, so both quantum cryptography and post-quantum cryptography (PQC) are advancing as complementary defences.
This feature explains the essentials: the concept of quantum cryptography, how it contrasts with conventional encryption, current progress, remaining obstacles, realistic timelines for mainstream use, and what individuals, organisations and governments should do to prepare.
Quantum cryptography covers methods that exploit quantum behaviour to perform secure communications. The best-known technique is quantum key distribution (QKD): two parties generate a shared secret using quantum states (for example, single photons). A key advantage is that any interception disturbs those quantum states, signalling an attempted eavesdrop.
Unlike traditional schemes that assume certain problems are hard to solve, quantum cryptography can provide information-theoretic security under defined models — meaning security rooted in physics, not in computational assumptions.
Beyond QKD there are other quantum primitives — quantum coin-flipping, quantum digital signatures — but the public and commercial focus centres on QKD alongside PQC. Post-quantum algorithms aim to be resilient to quantum attacks while remaining classical mathematical constructs.
Data encrypted today may be at risk tomorrow. Adversaries can capture ciphertext now and decrypt it later once quantum computers mature — the so-called “harvest-now, decrypt-later” problem. Records that must stay confidential for decades, such as patient files or sensitive archives, are especially vulnerable.
Essential services — energy grids, financial systems, transport control — depend on cryptographic safeguards. Should a sufficiently powerful quantum computer appear, it could undermine many authentication and signature schemes. That elevates quantum cryptography from niche research to an element of national digital resilience.
As everyday products become connected — from smart homes to vehicles — the demand for robust crypto increases. Adopting quantum-safe solutions before large-scale threats arrive will help preserve privacy and trust across consumer apps, identity systems and financial services.
Quantum cryptography remains concentrated in labs and targeted rollouts, but measurable advances are in evidence.
Pilot QKD networks exist in cities and across national borders. Fibre-based links and experimental satellite channels have exchanged quantum keys over significant distances, showing the physics works beyond controlled labs.
Standards bodies are progressing new algorithms designed to withstand quantum attacks, and several of these schemes are already finding their way into software and hardware stacks. Combining quantum cryptography with PQC is becoming the prevailing strategy.
Major firms, governments and cloud operators are launching migration efforts: auditing cryptographic assets, mapping upgrade paths and testing hybrid solutions that mix classical and quantum-safe techniques. The consensus is clear — preparation must start well before commercial quantum encryption is ubiquitous.
Quantum systems face physical limits: photon loss, noise and range constraints, plus the need for special components such as quantum repeaters or satellite relays. Scaling QKD to cover every connection or device is a major engineering and economic challenge.
Quantum hardware must overcome coherence and error-correction hurdles. The quantum machines that could realistically compromise today’s public-key systems may require millions of fault-tolerant logical qubits — a technological milestone that remains some years away. Similarly, quantum networks must reach high throughput and reliability to serve broad markets.
Standards for quantum-safe algorithms and networking are emerging, but global alignment and interoperable deployments will take time. Organisations need upgrade strategies that preserve compatibility and allow phased transitions.
Until hardware costs decline and the ecosystem matures, rolling out quantum cryptography across consumer devices and smaller organisations will remain costly and complex.
Predicting timelines is uncertain, yet expert surveys and roadmaps provide useful signposts.
“Q-Day” denotes the point when quantum machines can break current public-key systems. Many analysts place a non-negligible chance of this happening by the early to mid-2030s. The practical conclusion: quantum-safe measures should be widely adopted before such a milestone.
More pilot and regional QKD links (city and national networks) become operational.
Broad uptake of post-quantum algorithms across enterprises, governments and cloud platforms.
Initial consumer-facing quantum-safe features — software updates and secure hardware — appear for critical applications.
Expanded availability of QKD services for enterprises and high-value sectors, possibly under commercial subscription models.
Integration of quantum-safe methods into mainstream telecom, banking and IoT services.
Widespread migration away from legacy cryptographic standards; new deployments favour quantum-resistant schemes.
Global quantum networks capable of end-to-end quantum key exchange between devices.
Consumer hardware with built-in quantum-safe protections becomes common in phones, appliances and vehicles.
Data secured solely by classical crypto is either re-encrypted or treated as potentially exposed.
Overall: ubiquitous consumer-level quantum cryptography may be a decade or more away, but meaningful protection of critical systems is plausible by the early 2030s.
Look for updates and devices marketed as “quantum-safe” or “post-quantum.”
Choose services that demonstrate readiness for long-term data protection, especially for medical and financial records.
Remember that information encrypted today could be at risk in the future unless quantum-resilient protections are adopted.
Inventory cryptographic assets: which keys and algorithms protect what data, and how long that data must remain confidential?
Build crypto-agility so systems can swap algorithms and keys without costly redesigns.
Adopt hybrid encryption approaches now — combining classical and post-quantum methods — and plan to integrate quantum cryptography when feasible.
Prioritise protection of long-lived secrets; data with multi-decade sensitivity requires accelerated action.
Define standards for quantum-resistant algorithms and certify quantum-cryptographic solutions.
Support migration efforts and assist smaller organisations with funding and expertise.
Invest in national quantum-safe infrastructure for critical public services and sovereignty.
Educate citizens and industries: quantum readiness is a strategic issue affecting trust in digital systems.
Secure messaging platforms moving to quantum-resistant encryption so chat histories remain private over time.
Banking and payments adopting quantum-safe key exchange for transactions and digital wallets.
Telecommunications trialling QKD to bolster 5G/6G networks and protect undersea links.
IoT and connected devices embedding post-quantum algorithms in smart home hubs, vehicles and appliances.
Cloud providers offering quantum-safe storage and encryption for enterprise archives and backups.
Hardware bottlenecks: essential components like repeaters and fault-tolerant qubits are still under development.
Cost & economics: high prices could restrict consumer access until economies of scale are achieved.
Standards & regulation: inconsistent international rules may hinder global interoperability and rollout.
Legacy systems inertia: migrating entrenched infrastructure is expensive, risky and slow.
Awareness & readiness gap: underestimating the timeline risks leaving organisations exposed to future threats.
Quantum cryptography offers a shift from security based on computational hardness to protections founded on physical law. Translating laboratory breakthroughs into everyday products is a complex, multi-decade endeavour. While full consumer-level quantum encryption may be many years away, foundational work — pilots, standards and migration plans — is happening now.
Realistically, many critical systems could be using quantum-safe encryption by the early 2030s, with broader consumer availability following in the 2030s and beyond. The practical lesson is clear: organisations and users should begin preparing now to avoid leaving today’s sensitive data exposed to tomorrow’s quantum capabilities.
This article is for informational purposes only and does not constitute technical, legal or investment advice. Consult qualified cybersecurity and cryptography professionals or relevant authorities when assessing quantum-security needs for particular systems or data.









Zohran Mamdani Clinches NYC Mayoral Seat as Victory Speech Blends Politics and Bollywood
Zohran Mamdani won New York City's mayoral race, becoming the city's first Muslim and South Asian ma
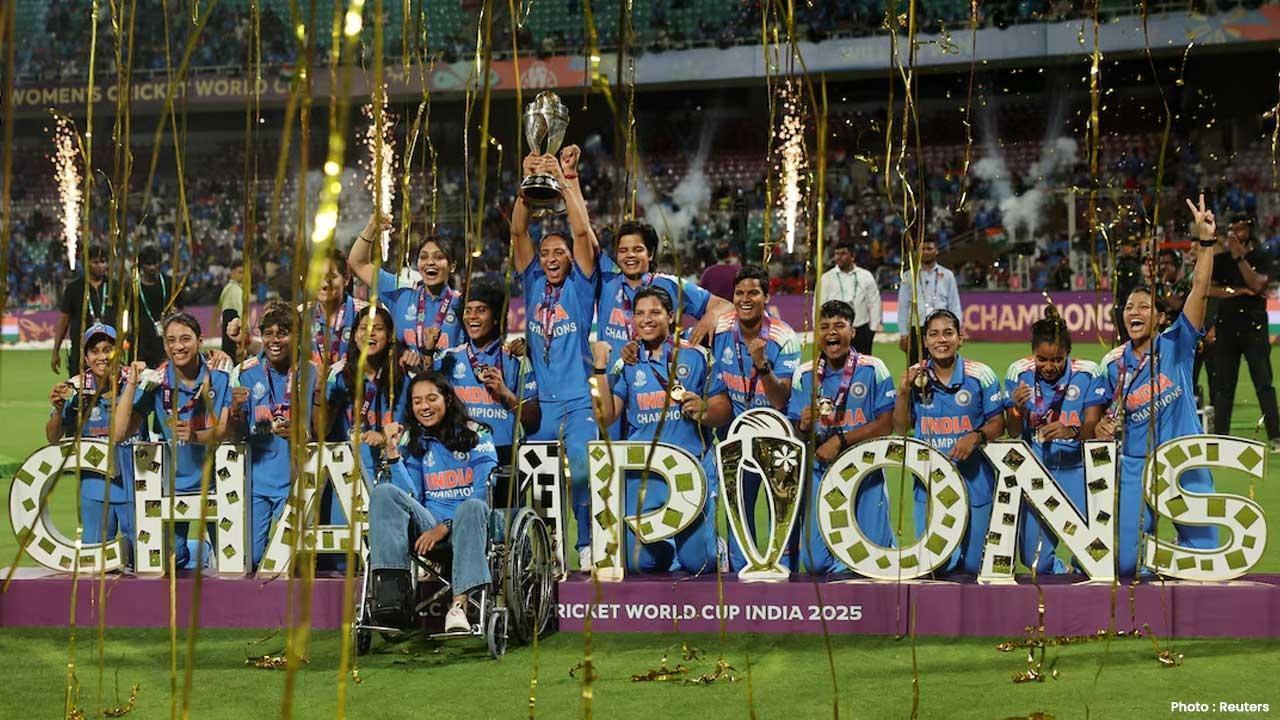
India Wins First Women’s World Cup 2025 Title
India lifts its maiden Women’s World Cup 2025 title! Harmanpreet Kaur’s team stuns South Africa in a

Manuel Frederick, 1972 Olympic Bronze Goalkeeper, Dies at 78
Manuel Frederick, a member of India’s 1972 Olympic bronze hockey team, has died in Bengaluru at 78 a

Muhammad Hamza Raja Wins IFBB Pro Card Puts Pakistan & UAE on Global Stage
Pakistani bodybuilder Muhammad Hamza Raja earns IFBB Pro Card in Czech Republic, showcasing Dubai’s

Shreyas Iyer’s Recovery Underway After Spleen Laceration in Sydney ODI
Shreyas Iyer is recovering after a spleen laceration sustained while taking a catch in the Sydney OD

Qatar Ready to Host FIFA U-17 World Cup 2025 in Aspire
Qatar confirms full readiness to host the FIFA U-17 World Cup 2025 from November 3–27, with world-cl